Featured Scientist

Author published in "Future Generation Computer Systems" affiliate to
Cheng-Chi Lee
Department of Library and Information Science,
Fu Jen Catholic University New Taipei City, Taiwan.
Article published in"Volume 93, April 2019, Pages 266-277"
Security enhancement on an RFID ownership transfer protocol based on cloud
Due to the advancement of convenience technology for people, the era of Internet of Things (IoT) has going on thriving, which has brought more and more attention to Radio Frequency Identification (RFID), as RFID is key to the sensor technology in IoT. As promoting of IoT, kind of protocols combine cloud to store authentication data and perform heavily computing which achieve the property of geographical restrictions in IoT. An ideal RFID system design should offer thorough protection in aspects of confidentiality, system security as well as user privacy. The protection should cover all functions and phases, among which is when the ownership is being transferred. A smooth ownership transfer mechanism can both help efficiently recycle used tags thus keeping the system cost down and provide the system with a high degree of flexibility so that different users other than the original owner can be properly authorized and then have a certain degree of control over the data and the sensors. So far, quite a number of studies about RFID ownership security issues have been brought up in the literature concerned with possible solutions provided; unfortunately, most of the existing ownership transfer protocols either come with some security weaknesses in the design itself and so are easy targets of attacks or cannot seem to fit in with the cloud environments. Recently, Cao et al. proposed an ingenious ownership transfer protocol, which still has some security flaws including vulnerability to the desynchronization attack as well as the tag impersonation attack and a tendency towards plaintext miscalculations. In this paper, we shall propose an improved, especially lightweight version of Cao et al.’s protocol we have developed on the basis of quadratic residues. With the identified security flaws mended, the improved protocol ensures a higher level of protection for ownership transfer at a much lower cost. Also included in this paper are some correctness and security analyses we have completed to prove the practicability of the proposed protocol. Moreover, we have compared the proposed protocol with some related works to show its superiority in terms of efficiency and scalability.[Full Article]
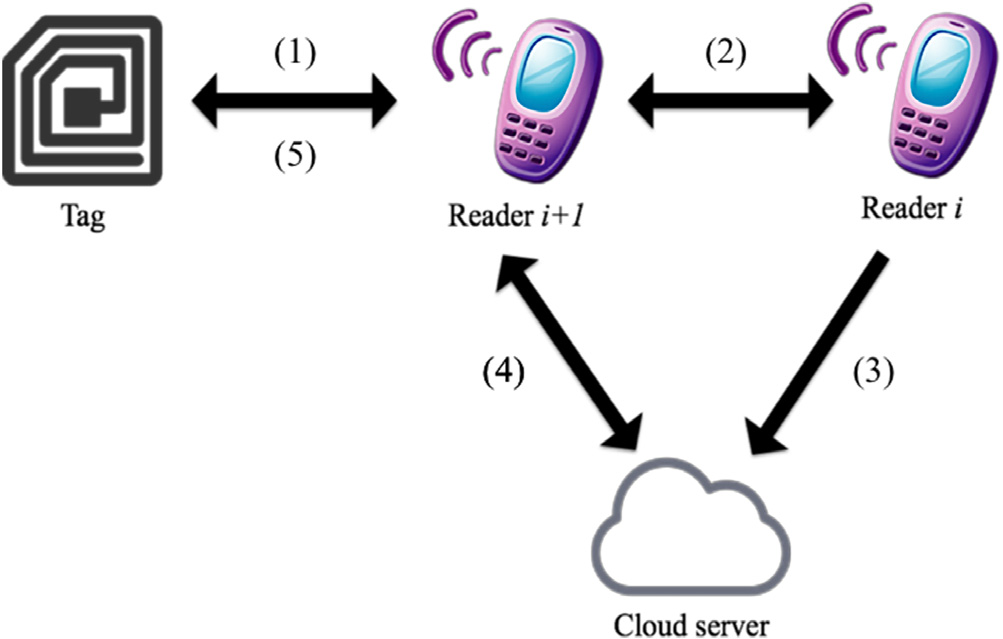
Fig. 1. Architecture of the proposed protocol.
42 views